Hammett's Glen
Computer Security: Chapter 1 - Changing Your Bad Habits
There's a Worm  Eating My Computer
Eating My Computer
And Other Tales From the Darkside
Computer security is something that doesn't come easy for some of us. It can be hard to understand and keep up with and a lot of us older computer users just don't quite get it. I've met many users that seem to think that using the Internet is like watching TV. Surfing various web-pages is analogous to changing channels and the page you are looking at is being "broadcast" from a station somewhere. Well unfortunately nothing could be further from the truth.The Internet is a two way street with code being constantly exchanged between your computer and dozens of servers, switches, routers, and isps all over the world. "packets" of information by the thousands are zipping all over the globe each second and each of these packets can contain personally identifying
So check this blog often and I will start with the basics and walk you through everything from virus protection to complete and total encrypted anonymity. - 09/08/09 - jinx
First:  Don't Touch That! You'll Get Burned!!!
Don't Touch That! You'll Get Burned!!!
First of all I’m going to assume that all of my readers here have a basic understanding of how to use a computer. How to do the fundamental things like use a mouse, point and click, copy and paste, cut and paste, left and right click, open a new window, execute an installation program, download files from the internet, etc. This is not a “How to Use Windows” blog so if you need to go back and refresh your computer skills now is the time to do it. Also it is being written for users of the Windows operating system though many of the tools and concepts will apply for Macs and Linux too. I am currently using Windows Vista 64 Ultimate SP2 on my desktop but I still use XP on my office computers and laptop. You should check your operating system and when I ask you to download certain programs, make sure you are getting the version that is compatible with your OS. And lastly, I make the obligatory disclaimer that I am not responsible for any damage, including loss of data, to your computer by following the instructions I suggest. Always take all necessary steps including creating restore points and backing up your data before making any changes to your computer.
A lot of people ask me, “How did things get so bad in the first place”? “Why did the people that invented the internet allow it to be so open that people could attack me to begin with”? Legitimate questions for sure but the fact is that what started out in the 60’s as an experimental way for researchers and scientists to quickly exchange information with each other grew into the incredibly huge network of millions and millions of independent computers we have today. Nobody planned it or saw it coming and nobody could possibly have imagined the form it would take. The standards on which the ‘Net operates were intentionally created open and insecure simply because it was easier and quicker for the guys that invented it to use. That very ease of use is what today’s crackers and virus writers exploit. The very thing that made it grow made it vulnerable. So the bottom line is: It is what it is. It’s up to you to figure out how to use it safely and securely.
The fact of the matter is that most people get infected the easiest way possible, they do it to themselves. That’s right. Most computers are infected by their owners. So the first and easiest way to improve your security is to improve your user habits by becoming more aware of the methods and techniques that malicious code writers use to get their mischief on your computer and then avoiding that behavior. So let’s start with some basic dos and don’ts:
1. Never, ever click on a link in an email. This type of email attack is called “phishing”. In what appears to be an innocuous or
2. Installing programs is another easy way to place ad-ware, spyware, and other little nasties on your box. Many times companies that make money selling info on your surfing and buying habits try to get you to install their “spy” programs on your computer by offering “free” software for your use. What you don’t know is that the “free” part comes with a caveat. In order to use the software you must give it permission to “phone home” usually under the guise of “…checking for updates”. Many times the software won’t work unless you grant these permissions. Don’t fall for it. The software is really reporting your personal usage habits back to a company or individual that then sells that info to marketers and spammers so they can send you targeted ads and spam, and that’s the good 

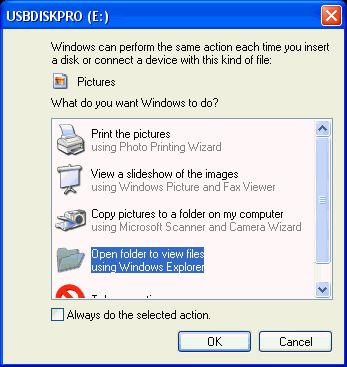
4. Disable any “autorun” options in your system. Windows lets you choose this option once when you first insert a CD or DVD or other non-system disk. While it is convenient to just insert a DVD and sit back and watch the movie, disabling autorun only adds one extra click and that is well worth the headache of cleaning up your computer after a worm or virus takes advantage of your gracious invitation to automatically install its business. Always run a scan of any new disk or USB storage device with your Anti-Virus Program before you run it. Even if it comes from a trusted source!
5. If someone sends you an attachment in e-mail or instant messaging, do not open it. If it is a picture, text or sound file (these attachments end in the extensions .txt, .jpeg, .gif, bmp, .tif, .mp3, .htm, .html, and .avi), you are probably safe, but still do a scan before opening. Many crackers know that people trust documents like those and they go out of there way to make you regret opening them. High risk file extensions include .exe, .bat, and .vbs, for their main purposes are to execute code, so the file openly admits that something will happen. You can negate the risk by preforming scans with your antimalware AND antivirus. If someone you know very well sends you a Word attachment or other type of file, e-mail them to ask them if they meant to send it to you. If they say yes, you can open it, but you might still be at risk if they are not good about running Anti-Virus scans or careful about what they download. Be wary of attachments with a double extension, such as .txt.vb or .jpg.exe, as the system will only recognize the extension to the extreme right, and run the file as such. Double extensions exploit an option in Windows to hide known file extensions thus hiding the second dangerous extension and showing only the first safe extension. Ensure that this option is disabled to more easily identify these files. Double extensions are often a good indicator that the file is malicious.
6. Many times computers are shared by family members in the same household and guests, such as visiting children and grandchildren, are allowed to use your computer. Trouble arises when guests use your computer un-supervised. My wife asked me to take a look at her mother’s computer. It seemed sluggish and unresponsive. I packed my usual toolbox of diagnostic software and began what I thought was going to be a routine one hour cache cleaning and defrag job. Seven hours later I finally had the problem licked! Several of her teenage grandchildren had been using the computer at night after everyone had gone to bed and had visited some pretty disgusting places on the net. Along the way the computer had become infected with at least three well known viruses, dozens of “tracking cookies”, and the temporary caches were overflowing with images and websites that left little to the imagination. She now forbids anyone from using her computer when they visit and made sure everyone knows why. I suspect a few teeny butts got grounded pretty hard by some rather embarrassed parents. So if you are going to let guests use your computer, be sure to set up the “Guest” account available on XP and Vista. Do not let anyone use it un-supervised or sign in as an “Administrator”. The best policy is to set up a different account for each user and keep “Administrator” rights off limits to everyone but you.
7. Don’t reuse passwords. A lot of sites require you to sign up for an account and create a password. Don’t use your email account password for your online banking account. Get a program to manage your passwords and use a different password for each site. Most of these password programs will generate a long random password that can’t be guessed. (Three good ones are 1Password for the Mac, Personal Passworder for Windows and ,my favorite Keypass ) Keypass is free open source software and the other two are for sale. - 09/10/09 - jinx
8. When going to secure sites, like banks or sites to purchase items, make sure you have a secure connection when you are about 
9. Keep your computer Operating System (OS) up-to-date. Don’t disable or put off updates your OS vendor sends. I always keep Automatic Updates set to "Notify" That way I am aware when updates are available but can install them when I'm not busy. Chances are they are patching a problem that is currently being exploited. Keep your applications up-to-date. Especially your Virus Software. You should always set your Virus Software to automatically update. In the past you may have put off updating to the latest Adobe Reader because you didn’t see any problems with the one you’re using. Now the update may include a security fix too.
10. Don't go to porn sites. They're boring, pointless, and almost all of them are dangerous. Plus it'll drive you crazy.
----------- 09/10/09--------- jinx
Photo credits: WSPA, PixUnlimited, Tony Jones, Microsoft, Adobe.
Last updated on 09/14/2009